Update 2: After writing this post, I also discovered another vulnerability in Trivia Crack that allowed for giving users unlimited lives/spins. At that time, I added this as another feature to Trivia Cracker. Yesterday (1/29/2016), Trivia Cracker started preventing this feature (automatic question answering continues to work — as described in this post). But what’s funny is, in addition to preventing it, the Trivia Crack server also calls me out specifically!
Update 1: Using similar techniques to the below, I’ve also released a cheating Chrome extension for Candy Crush. Get it here.
As the holiday season began a few weeks ago, I started to notice that a new app, Trivia Crack, was becoming popular with my friends. For those of you who don’t know, Trivia Crack is a new game for Android, iPhone, and Facebook. The premise of the game is simple, and very similar to another popular app from last year, QuizUp. Essentially, you answer trivia questions of various categories, competing against your friends for bragging rights. Despite the simplicity (or maybe due to it), Trivia Crack has become very popular as of late – racking up 5.3 million likes on Facebook and becoming the top free app in the Google Play (Android) store.
You’d think the developers of such a polished and successful game might have taken the time to implement it in a way that is secure from cheating, but it turns out writing a program to cheat at Trivia Crack is actually fairly simple. Over the course of a weekend, I was able to write and release a Chrome extension, Trivia Cracker, that turned me from a medicore-at-best Trivia Crack player to a seemingly genius demigod. You can see Trivia Cracker in action below:
So what’s wrong with Trivia Crack’s implementation that allowed me to so easily build a tool that lets anyone cheat? In short – when the Trivia Crack client requests from the Trivia Crack server the next question to ask the user, the server responds not just with the question and the possible answers, but also sends which answer is the correct answer. The details of the vulnerability, how I found it, and how I built a Chrome extension to take advantage of it are below.
1 – Finding the vulnerability
After losing to my friends in Trivia Crack one too many times, I decided I wanted to see if I could win in my own, special way. While I’m not so good at random trivia, I am pretty good at reverse-engineering. I suspected I might be able to take advantage of sending my own requests to Trivia Crack’s servers, or using some data in the responses from Trivia Crack’s servers, to gain an edge in the game. So I started by researching what kinds of data the Trivia Crack client and server pass back and forth.
To inspect this data, I played Trivia Crack in my browser on Facebook, while recording and inspecting the requests and responses sent between Trivia Crack’s client and server using a tool I’d created previously called Gargl. Yes, I know I could have used Fiddler or Chrome’s Developer Tools to do the same. I decided to use Gargl instead because in addition to letting you view client/server requests/responses, Gargl also lets you modify and parameterize these requests, and then auto-generates modules in a programming language of your choice so you can make these same requests without writing a line of code. More on that later.
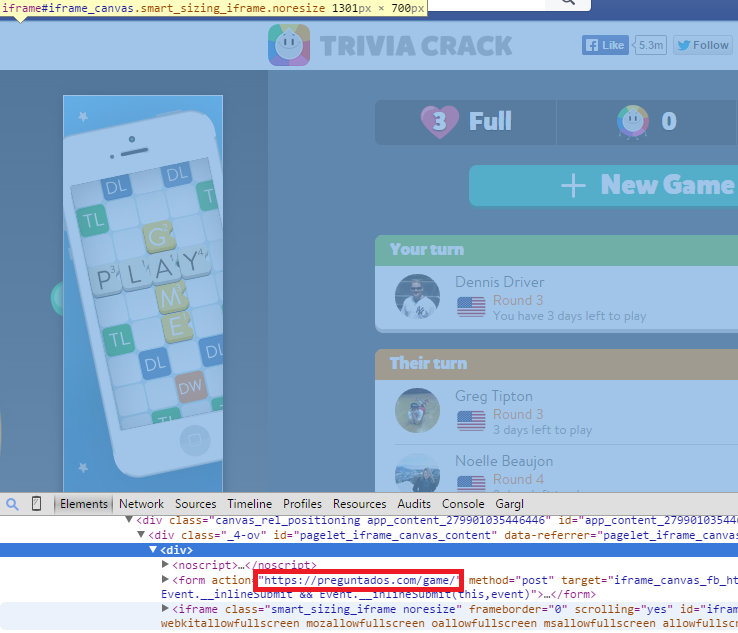
Anyway, after telling Gargl to start recording and going to Trivia Crack on Facebook in my browser, the first step was to figure out which of the many requests being sent on this Facebook page were related to Trivia Crack, versus Facebook itself. Inspecting the HTML on the page showed that the Trivia Crack content is embedded into Facebook via an iframe. The element right above this iframe was a form meant to post to a peculiar URL- https://preguntados.com/game.
My limited knowledge of Spanish reminded me that “pregunta” means “question,” which seems related to trivia, so I suspected this was the domain where Trivia Crack is hosted. Going to the https://preguntados.com/game URL confirmed that suspicion:
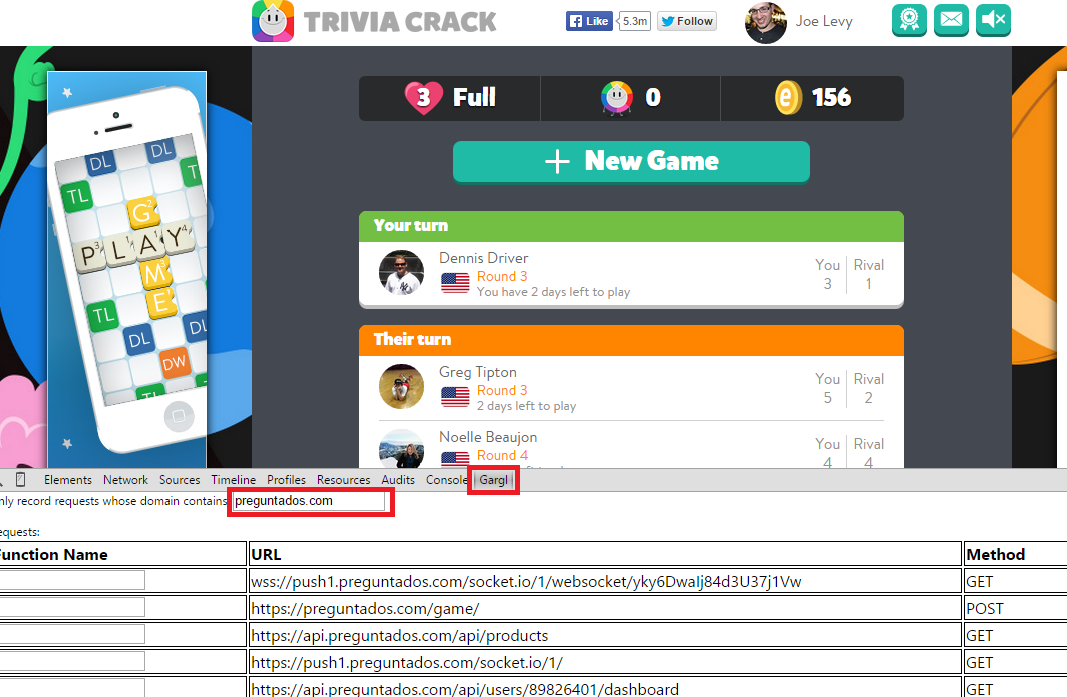
The next step was just to start playing Trivia Crack, and as I played look at the requests Gargl finds that the page is making to any url containing “preguntados.com”:
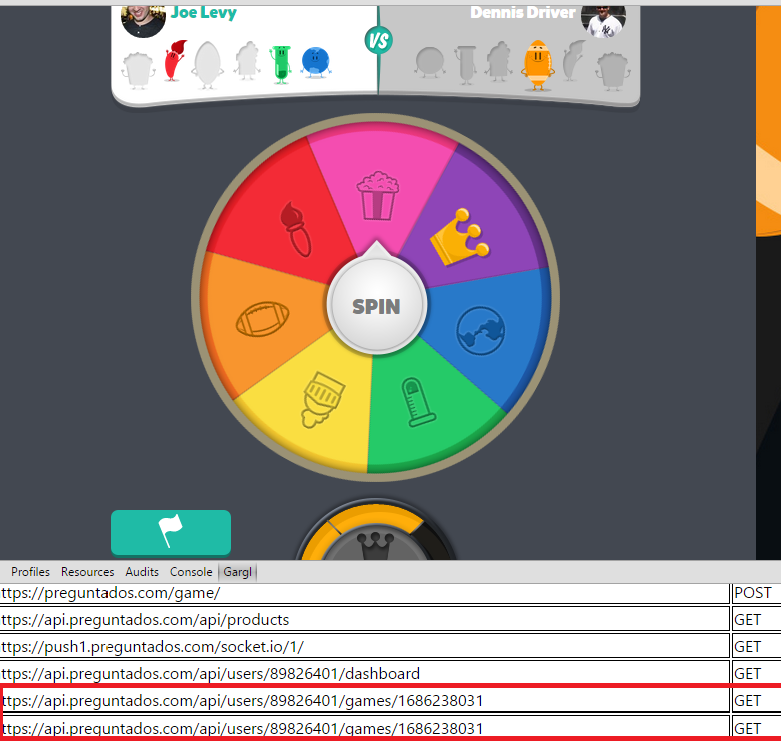
As I answered Trivia Crack questions, I noticed a new request seemed to be issued for each question. Actually, the request seemed to be issued before I even “spun the spinner” in Trivia Crack to determine what category the next question would be:
This made me think maybe the questions were predetermined, and the “random spinner” in fact was predetermined to land on a certain category (and ask a certain question) based on the response from the server to the “api.preguntados.com/api/users/<userID>/games/<gameID>” request that sent before you click the “Spin” button. To me, this meant I could probably alert the user to the question they are about to be asked ahead of time, so they would have as much time as they wanted to think about it or look it up. This would be an advantage because in Trivia Crack, you only get 30 seconds to answer a question once the question is shown, to prevent the user from looking up answers. In addition, in some game modes its not just the number of questions you get correct, but also the amount of time you take to answer, that determines if you win. If I could show the user the question ahead of time, they could obviously answer it much more quickly once Trivia Crack itself shows the question.
So I figured I had a lead and dug into the details of this request. It turns out this request actually provided a much larger “cheater’s advantage” than I thought…
2 – The vulnerability in detail
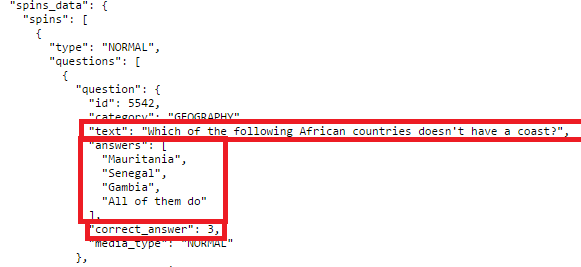
Using Gargl to look at the “api.preguntados.com/api/users/<userID>/games/<gameID>” request/response in detail, I was able to confirm that it does indeed provide the question to be asked, as well as the possible answers, in the response. However, I was surprised to find that the correct answer to the question is also embedded in the response!
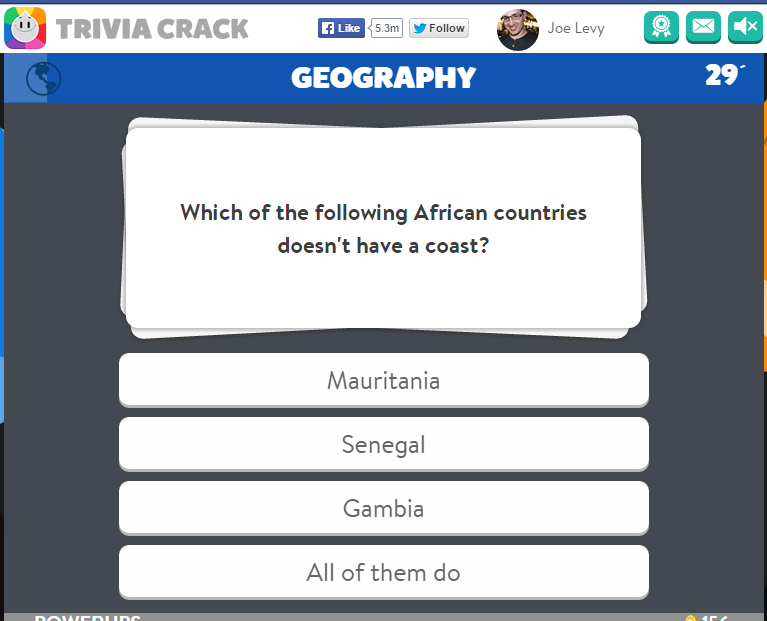
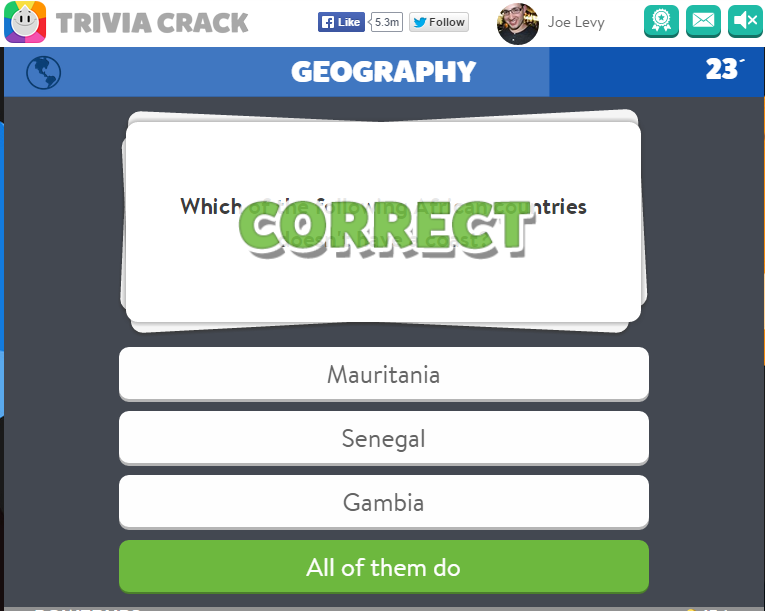
As you can see above, the response to this request contains the question, the possible answers, and which index in the array of possible answers is the correct answer. So if this data is indeed about the next question, after I click “Spin,” I should be asked “Which of the following African countries doesn’t have a coast?” and the correct answer should be answers[3] from above, which is “All of them do”. Clicking “Spin” proved this hypothesis correct:
I also used my browser to find that repeated GET requests to “api.preguntados.com/api/users/<userID>/games/<gameID>” always give the same response, until you answer the question it provides. This means I could request this URL from my own tool and still receive the same question as the Trivia Crack client on Facebook would receive.
A response containing the correct answer, when the goal is that the user must determine the answer themselves, is in direct conflict with the “Defensive Programming” practice of programming – particularly the “never trust the client” web programming principle. Since the server has no control over how the client acts, it can’t assume the client will not act in a malicious way, and so must protect itself. The correct way of implementing answer checking behavior is to do it on the server side. Don’t send the correct answer to the client at any point, and instead make the client send the user’s answer to the server, where the server will then check it for correctness and credit the user if correct (and of course, only allow one answer to be sent per user per question).
However, Trivia Crack did not do this, and instead trusts the client. Now it was just a matter of creating a malicious client to take advantage of the fact that the correct answer is sent in the response. Ideally, one that would be easy for non-technical users to install and use. Hmm…how about a Chrome extension that just adds a button to the Trivia Crack game, when played on Facebook, that when clicked answers the current question correctly automatically??
3 – Taking advantage of the vulnerability
As I mentioned above, Gargl allows you to take the requests you had it record, modify and parameterize them as needed, and then auto-generate modules in a programming language of your choice to make these same requests. I’m not going to go into the details of that process since you can look at one of my Gargl blog posts to find that info, but essentially I generated a Gargl template file for Trivia Crack‘s various API requests, using the Gargl Chrome extension, and then used a Gargl generator to turn that template file into a Trivia Crack JavaScript library. Using Gargl for this allowed me to create a JavaScript library that talks to Trivia Crack’s servers, without writing a line of code to do so, and also have a template file around for the future in case I want to do the same thing later for another programming language.
Once I had this Trivia Crack JavaScript library, it was a simple matter of building a Chrome extension in JavaScript that runs on the domain loaded in the Trivia Crack Facebook game page iframe (preguntados.com), adds a button to the HTML for the game, and when that button is clicked requests the “api.preguntados.com/api/users/<userID>/games/<gameID>” URL, parses the response for the correct answer, and then clicks the answer button on the page representing the correct answer.
And just like that, Trivia Cracker was born! Curious about the exact details of how Trivia Cracker works? Check out the source code on GitHub.
Interested in hearing about other side projects like this one? Subscribe to my blog and follow me on Twitter. I’ll let you know when I think of something fun.


You have discovered the cold water.
Yes, is easily to doubt that the game is well programmed and uncheateable when somebody you know is not a super smart guy beat you in seconds..
That’s why I stopped playing Trivia Crack and I’m doubtful if they will correct their app since I reported this on May 2014.
But anyway, is good to know that somebody else found the bug and not just found it, actually made a chrome extension, lol.
That’s why I stopped playing Trivia Crack and I’m doubtful if they will correct their app since I reported this on May 2014.
But anyway, is good to know that somebody else found the bug and not just found it, actually made a chrome extension, loll
That’s nothing. I’ve found a way to cheat at solitaire! You wouldn’t believe the vulnerabilities it has.
This may be the greatest response ever.
Excellent article. What a fun idea for a “hack” 😛
Hey Joe,
I was wondering if there was a simple way to add more lives or reduce the wait time, so I can use this method until your chrome extension is updated.
Thanks!
Very very doubtful. The reason this “hack” works is because it’s simply looking at information you already have, hidden behind a curtain. If you know how to look for it, it’s there. You’re talking about modifying data that’s held on a server which is a different beast entirely.
I agree, however if you look at his extension description it says that he will soon be adding infinite lives, powerups and etc.
I actually attempted this and was able to manipulate the responses from the Trivia Crack server in real time to contain 99999 for the lives, coins, and spins. The Trivia Crack client accepted these values and showed them in the UI, but when you use a life, coin, or spin, it tells the server you are using one and the server responds with an error saying you don’t have any left, at which point the client rejects your attempt.
So while Trivia Crack doesn’t validate answers server side, it turns out they do validate lives, coins, and spins!
Perhaps this is an amateur guess, but could they be using a byte or some small variable type to store these, and you’re overflowing to numbers <1?
Interesting idea Harris. I don’t think that is the case though because that 99999 value is never sent to the server, it is only received by the client. The 99999 value lets you get past client side checks for things like “does this user have enough lives left to allow them to start a new game,” but then once a user clicks the new game button, the client tells the server “this user wants to start a new game,” and the server, which knows the real # of lives one has left, also validates one has enough lives left to start a new game, and responds to the client “sorry, not enough lives.”
So I think its just simply server side validation, rather than a byte overflow.
Hey Joe, awesome article about the behind-the-scenes vulnerabilities of Trivia Crack! Would it be possible to insert your own questions this way? I’m a senior in high school hoping to eventually get my master’s in Cyber Security, and I’m pretty well known at school for my reputation as a geek. I want to ask a girl at school to go to prom with me using Trivia Crack (She would spin the wheel, and the question would be “Will you go to prom with me?” The answers would include two “Yes” options and two “No” options. When she presses yes, it would show up as correct.) I know this wouldn’t work on an online version of the game, but would it work as an offline mode (I could download the source code and edit it)? I also have a jailbroken iPhone, a rooted Android phone, a Mac Pro, and a PC, so devices aren’t a problem. Thank you in advance!
Hi Curtis,
Fun idea. How much time do you have? I have a pretty good idea of how to do this with the online version of the game on Facebook, that might work. Only issue is she would have to access the game on Facebook, and using the Chrome browser started in a special way (so probably from your laptop, unless you have access to hers to set this up). Also, only one answer can be correct, not two, so there would only be one “yes” option.
Find my email on http://jodoglevy.com/ . Always happy to help out an aspiring engineer.
Interesting! I actually found and exploited this glitch myself, though it was time consuming to sift through the responses manually. Thanks for this extension
So I have to be using Chrome Browser in order to be able to download the Trivia Cracker? It’s not an app that’s available from play store to be used with the game app?
I was also hoping for an app version of this. Any chance of that being a possibility?
Boooooo! Why would you make a cheat for such a simple game meant to be fun… If I used this crack I’d feel like a real loser… I won’t even buy coins because even that seems weaksauce. Save the cheats for Call of Duty.
Do u think garlg can be used to bypass captchas? maybe just some of them? Any idea or test is more than welcome thanks in advance
thanks in advance
Hmmm . . . I wonder why it is that some people are programmed to cheat? Why is the “win” so important rather than the challenge? I realize that if SOME are playing against cheaters, then you just never win. Takes all the fun out of the game. But that’s sad, because it’s a lot more fun just to play, win or lose, and if anything, challenge yourself.
But we live in a society now where the mentality is everyone thinks they deserve a trophy even if they lose. There’s no challenge left in life to STRIVE to be better. You just cheat to win and cheat to get ahead. It’s happening in our high schools, our colleges, it’s rampant in our government, and it’s a trend that hurts society in the long run, and your intelligence. We’re dumbing down society.
By the way, in the article it’s “mediocre” not — “. . . turned me from a MEDICORE-at-best Trivia Crack player. . .” Just sayin’.
THANK you.
THANK YOU
nice trick..thanks for Cracking Trivia Crack
Bravo! Nice, dude!
Hey Joe, nice work on the extension! Listen I’m trying to get what you did right above here, and it seems that the game has updated, it doesn’t generate the ”process” before the spin with the right answer, but your extension still gets it, which means that there’s still a way that you know that I would like to if possible. How do you ”read” what gargl has on? Also, couldn’t you work on maybe a way to lower the price on the card machines? Thx
The extension works the same way as it always has — when you click the Trivia Cracker button it requests the current question for the game, as described above, grabs the correct answer out of the response to that request, and then selects that answer on the page.
I’m not sure what you mean by “‘read’ what gargl has on”.
I open the game, follow what you did, and I can’t find where the answer of the question on gargl. Do you think doing something with the gems is possible? I kind of investigated by my little knowledge, and it’s like the questions : when you click on the card to buy, the process has already happened, they are identified with an ID (not sure yet what’s for) and their number, so basically you can create a command to get any card you want.
This may be the greatest response evers
Hello, answer button doesn’t work sometimes, it keeps saying “we were unable to validate your license” even though i bought the app, i am signed in to gmail too. Can you help please?
Thanks
Hallo, thank’s a lot! I beat 1910 level, but i don’t open 1911…. Help, please….
I beat 1910 level, but i don’t open 1911…. Help, please….
I had several cards giving me free spins after the allotted time, now my cards only have lives and gems. I sure wish I knew ho to get my free spins back, thoughts?